As technology continues to evolve, connecting devices remotely through IoT (Internet of Things) has become increasingly important for businesses and individuals alike. However, managing remote connections while maintaining security, especially when operating behind a firewall, can be challenging. This article will guide you step-by-step on how to use RemoteIoT behind a firewall on Windows, ensuring a secure and efficient connection.
RemoteIoT is a powerful tool that allows you to manage IoT devices from anywhere in the world. Whether you're monitoring smart home devices, industrial equipment, or any other connected gadget, RemoteIoT provides a seamless solution. However, setting it up behind a firewall requires specific configurations to ensure both accessibility and security.
In this article, we will explore the technical aspects of configuring RemoteIoT on Windows while navigating through firewall restrictions. By the end of this guide, you'll have all the knowledge necessary to set up a secure and functional remote IoT system. Let's dive in!
Table of Contents
- Introduction to RemoteIoT
- Understanding Firewalls
- Preparing Your Windows Environment
- Configuring RemoteIoT
- Firewall Settings for RemoteIoT
- Securing Your Connection
- Troubleshooting Common Issues
- Advanced Techniques
- Performance Optimization
- Conclusion and Next Steps
Introduction to RemoteIoT
RemoteIoT is a cutting-edge platform designed to facilitate remote management of IoT devices. It enables users to control and monitor devices from any location, making it an essential tool for modern businesses and tech-savvy individuals. With RemoteIoT, you can manage everything from smart home appliances to industrial machinery with ease.
Key Features of RemoteIoT
- Secure connection protocols
- Real-time monitoring capabilities
- Customizable dashboards
- Support for multiple device types
Despite its versatility, RemoteIoT requires specific configurations when used behind a firewall, particularly on Windows systems. Understanding these configurations is crucial for ensuring seamless operation.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls play a vital role in protecting your network from unauthorized access and potential cyber threats. When using RemoteIoT behind a firewall, it's important to configure the firewall to allow necessary traffic while maintaining security.
Types of Firewalls
- Packet-filtering firewalls
- Stateful inspection firewalls
- Next-generation firewalls
For this guide, we will focus on configuring Windows Firewall, which is a built-in feature of the Windows operating system.
Preparing Your Windows Environment
Before configuring RemoteIoT behind a firewall, ensure your Windows environment is properly set up. This includes installing the necessary software and verifying system requirements.
System Requirements
- Windows 10 or later
- RemoteIoT software installed
- Administrator privileges
Additionally, make sure your system is updated with the latest security patches and software updates.
Configuring RemoteIoT
Once your environment is ready, you can proceed to configure RemoteIoT. This involves setting up the application to work efficiently within your network.
Step-by-Step Configuration
- Download and install RemoteIoT from the official website.
- Launch the application and create an account if you haven't already.
- Connect your IoT devices to the platform.
- Configure device settings according to your needs.
Proper configuration ensures that RemoteIoT functions correctly, even when operating behind a firewall.
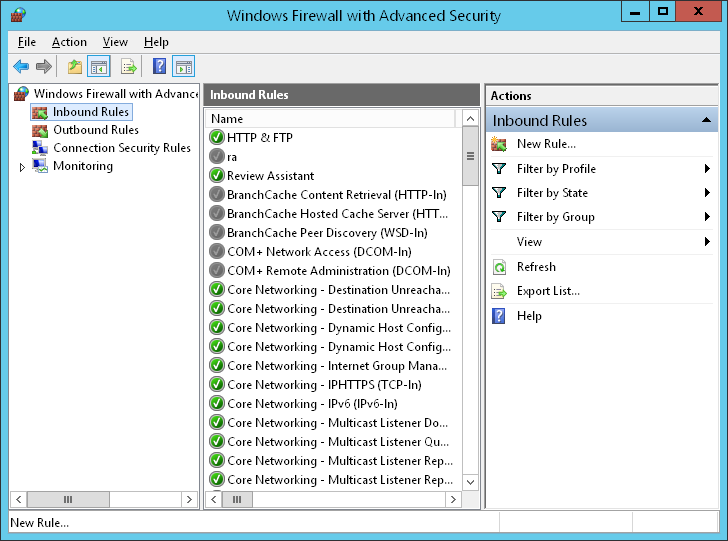
Firewall Settings for RemoteIoT
Configuring Windows Firewall is a critical step in using RemoteIoT behind a firewall. This involves allowing specific ports and applications through the firewall to ensure smooth communication.
Allowing RemoteIoT Through the Firewall
- Open Windows Defender Firewall.
- Click on "Allow an app or feature through Windows Defender Firewall."
- Select RemoteIoT from the list of applications or add it manually.
- Ensure both private and public networks are checked.
By allowing RemoteIoT through the firewall, you enable it to communicate with your IoT devices securely.
Securing Your Connection
Security is paramount when managing IoT devices remotely. Implementing robust security measures ensures that your data and devices remain protected from potential threats.
Best Practices for Securing RemoteIoT
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication whenever possible.
- Regularly update software and firmware.
- Monitor network activity for suspicious behavior.
By following these best practices, you can significantly enhance the security of your RemoteIoT setup.
Troubleshooting Common Issues
Even with proper configuration, issues may arise when using RemoteIoT behind a firewall. Below are some common problems and their solutions.
Issue: Unable to Connect to Devices
Solution: Verify that the necessary ports are open in the firewall settings. Additionally, ensure that the RemoteIoT application is allowed through the firewall.
Issue: Slow Connection Speed
Solution: Optimize your network settings and ensure that your internet connection is stable. Consider upgrading your bandwidth if necessary.
Addressing these issues promptly can help maintain a smooth and efficient RemoteIoT experience.
Advanced Techniques
For users seeking more advanced functionality, there are several techniques to enhance your RemoteIoT setup. These include setting up a virtual private network (VPN) and implementing advanced firewall rules.
Setting Up a VPN
A VPN provides an additional layer of security by encrypting your internet traffic. This is particularly useful when managing sensitive IoT devices.
Advanced Firewall Rules
Creating custom firewall rules allows you to fine-tune your security settings, ensuring that only necessary traffic is allowed through the firewall.
Performance Optimization
Optimizing the performance of your RemoteIoT setup can lead to improved efficiency and reliability. Consider the following tips:
Tips for Performance Optimization
- Minimize unnecessary background processes.
- Optimize device configurations for better performance.
- Regularly clean up logs and temporary files.
By implementing these optimizations, you can enhance the overall performance of your RemoteIoT system.
Conclusion and Next Steps
In conclusion, using RemoteIoT behind a firewall on Windows requires careful configuration and attention to security. By following the steps outlined in this guide, you can set up a secure and efficient remote IoT system. Remember to regularly update your software and monitor your network for any potential threats.
We encourage you to leave a comment below if you have any questions or feedback. Additionally, feel free to share this article with others who may find it helpful. For more information on RemoteIoT and related topics, explore our other articles on the site.
References: