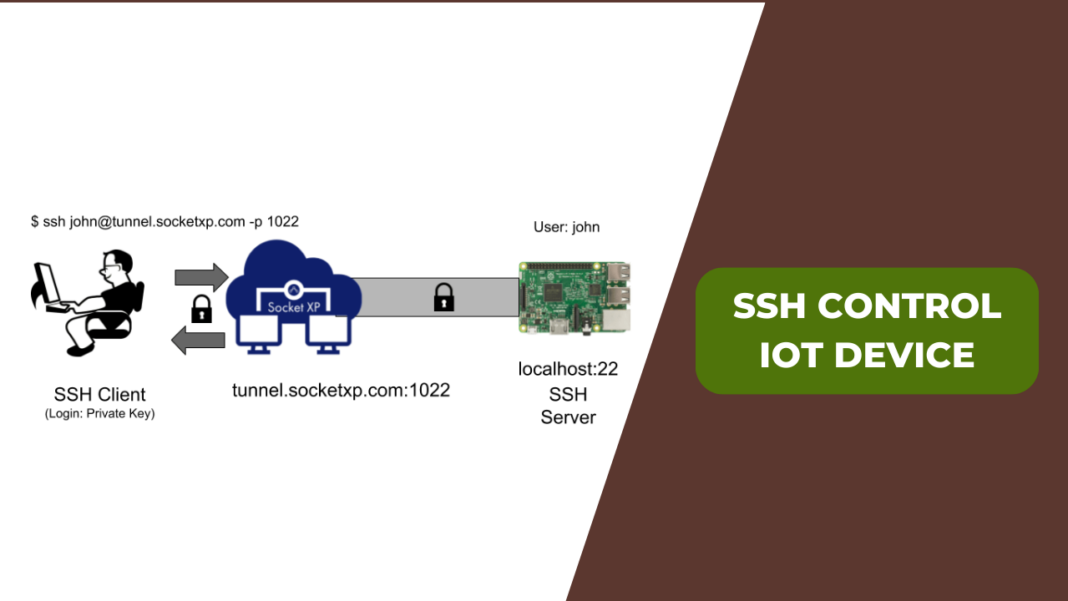
In the rapidly evolving world of technology, SSH remote IoT device management has become a critical tool for professionals and enthusiasts alike. As the Internet of Things (IoT) continues to expand, understanding how to securely access and manage remote devices is no longer optional—it's essential. Whether you're configuring smart home devices or managing industrial sensors, SSH provides a robust framework for ensuring data integrity and security.
Secure Shell (SSH) is more than just a protocol; it is a gateway to seamless device management across networks. By leveraging SSH, users can remotely control IoT devices with confidence, knowing that their communications are encrypted and protected from unauthorized access. This article will delve into the intricacies of SSH remote IoT device management, providing actionable insights and expert advice to help you harness its full potential.
Whether you're a seasoned IT professional or just beginning your journey into IoT, this guide will equip you with the knowledge needed to navigate the complexities of remote device access. From setting up SSH connections to troubleshooting common issues, we'll cover it all. Let's explore how SSH can revolutionize the way you interact with your IoT ecosystem.
Understanding SSH and Its Role in IoT
What is SSH?
Secure Shell, commonly referred to as SSH, is a cryptographic network protocol designed to facilitate secure communication over unsecured networks. Originally developed in 1995, SSH has since become the gold standard for remote device management. Its primary function is to establish encrypted connections between a client and a server, ensuring that sensitive information remains private and tamper-proof.
For IoT devices, SSH serves as a vital tool for maintaining security while enabling remote access. Unlike traditional methods such as Telnet, which transmit data in plain text, SSH encrypts all data exchanged between the client and the device. This encryption ensures that even if an attacker intercepts the communication, they won't be able to decipher the transmitted information.
Why SSH is Essential for IoT Devices
In the realm of IoT, security is paramount. Devices connected to the internet are inherently vulnerable to cyber threats, making secure communication protocols like SSH indispensable. Below are some reasons why SSH is crucial for IoT:
- Encryption: SSH encrypts all data exchanged between the user and the IoT device, preventing eavesdropping and data theft.
- Authentication: SSH employs robust authentication mechanisms, such as public-key cryptography, to verify the identity of both the user and the device.
- Command Execution: SSH allows users to execute commands on remote devices securely, enabling efficient management and troubleshooting.
- File Transfer: With SSH, users can securely transfer files to and from IoT devices using protocols like SFTP (SSH File Transfer Protocol).
Setting Up SSH for Remote IoT Device Management
Prerequisites for SSH Configuration
Before diving into the setup process, it's important to ensure that your IoT device supports SSH. Most modern IoT devices come equipped with SSH capabilities, but older models may require additional software or firmware updates. Below are the prerequisites for configuring SSH:
- An IoT device with SSH enabled or capable of enabling SSH.
- A stable internet connection or local network access.
- A client device (e.g., laptop or smartphone) with an SSH client installed, such as PuTTY or OpenSSH.
- A basic understanding of networking concepts and command-line interfaces.
Step-by-Step Guide to Configuring SSH
Configuring SSH for your IoT device involves several straightforward steps. Follow this guide to establish a secure connection:
- Access your IoT device's settings menu and enable SSH. This step may vary depending on the device's operating system.
- Identify the device's IP address, which will serve as the connection endpoint.
- Install an SSH client on your client device if one isn't already installed.
- Open the SSH client and input the device's IP address, port number (usually 22), and authentication credentials.
- Establish the connection and begin managing your IoT device remotely.
Best Practices for Securing SSH Connections
Implementing Strong Authentication
One of the most effective ways to secure SSH connections is by implementing strong authentication mechanisms. Public-key cryptography is widely regarded as the gold standard for SSH authentication. Instead of relying on passwords, users can generate public and private key pairs, significantly reducing the risk of brute-force attacks.
To set up public-key authentication:
- Generate a key pair using tools like ssh-keygen.
- Copy the public key to the IoT device's authorized_keys file.
- Disable password authentication to further enhance security.
Configuring Firewall Rules
Firewalls play a critical role in protecting SSH connections from unauthorized access. By configuring firewall rules, users can restrict incoming SSH connections to trusted IP addresses or networks. This approach minimizes the attack surface and ensures that only authorized users can access the IoT device.
Common Challenges in SSH Remote IoT Device Management
Troubleshooting Connection Issues
Despite its robust design, SSH connections can sometimes encounter issues. Below are some common problems and their solutions:
- Connection Refused: Ensure that SSH is enabled on the IoT device and that the correct IP address and port number are being used.
- Authentication Failure: Verify that the correct credentials or key pair are being used for authentication.
- Timeout Errors: Check the network connection and ensure that there are no firewall rules blocking the SSH port.
Addressing Security Vulnerabilities
As with any technology, SSH is not immune to vulnerabilities. Staying informed about the latest security patches and updates is crucial for maintaining a secure connection. Regularly updating the SSH server and client software can help mitigate potential risks.
Advanced Techniques for Enhancing SSH Performance
Optimizing SSH Configuration
To improve the performance of SSH connections, users can modify the SSH configuration file (sshd_config). Below are some optimizations to consider:
- Disable unused authentication methods, such as host-based authentication.
- Enable compression for faster data transfer over slow networks.
- Set a timeout value to automatically disconnect idle sessions.
Implementing SSH Tunnels
SSH tunnels provide an additional layer of security by encrypting all traffic between the client and the IoT device. This technique is particularly useful when accessing devices over public networks. By setting up an SSH tunnel, users can ensure that their communication remains private and secure.
Real-World Applications of SSH in IoT
Smart Home Automation
SSH plays a pivotal role in smart home automation by enabling remote access to smart devices. Homeowners can use SSH to monitor and control their smart thermostats, lighting systems, and security cameras from anywhere in the world. This convenience not only enhances user experience but also improves energy efficiency and security.
Industrial IoT Solutions
In industrial settings, SSH is used to manage and monitor critical infrastructure such as sensors, actuators, and control systems. By leveraging SSH, engineers can perform remote diagnostics and maintenance, minimizing downtime and maximizing productivity.
Data Security and Privacy in SSH Remote IoT Device Management
Protecting Sensitive Information
Data security is a top priority when managing IoT devices remotely. SSH ensures that sensitive information, such as configuration files and log data, remains secure during transmission. By adhering to best practices and regularly auditing SSH configurations, users can safeguard their IoT ecosystems against potential threats.
Compliance with Industry Standards
Organizations utilizing SSH for IoT device management must ensure compliance with relevant industry standards and regulations. This includes adhering to guidelines set forth by bodies such as the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO).
Future Trends in SSH and IoT
Emerging Technologies
As technology continues to evolve, new advancements in SSH and IoT are on the horizon. Quantum-resistant cryptography, for example, promises to revolutionize the way we secure SSH connections in the post-quantum era. Additionally, the integration of artificial intelligence (AI) and machine learning (ML) into SSH protocols could enhance threat detection and response capabilities.
Challenges and Opportunities
While the future of SSH in IoT looks promising, challenges such as increasing cyber threats and the growing complexity of IoT ecosystems must be addressed. By embracing emerging technologies and adhering to best practices, users can unlock the full potential of SSH in the IoT landscape.
Conclusion
In conclusion, SSH remote IoT device management is a powerful tool that enables secure and efficient device access across networks. By understanding the fundamentals of SSH and implementing best practices, users can enhance the security and functionality of their IoT ecosystems. Whether you're managing smart home devices or overseeing industrial infrastructure, SSH provides the tools needed to succeed in the modern digital age.
We invite you to share your thoughts and experiences with SSH remote IoT device management in the comments below. For more insightful articles on technology and IoT, be sure to explore our other content. Together, let's build a safer, smarter, and more connected world.
Table of Contents
- Understanding SSH and Its Role in IoT
- Setting Up SSH for Remote IoT Device Management
- Best Practices for Securing SSH Connections
- Common Challenges in SSH Remote IoT Device Management
- Advanced Techniques for Enhancing SSH Performance
- Real-World Applications of SSH in IoT